XTEA
|
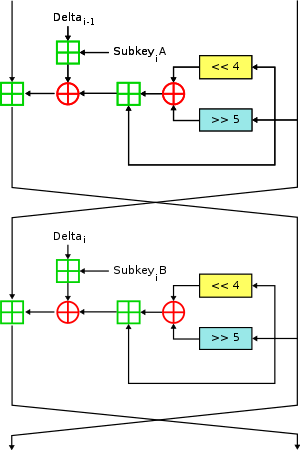
Two Feistel rounds (one cycle) of XTEA
|
|
| General | |
|---|---|
| Designers | Roger Needham, David Wheeler |
| First published | 1997 |
| Derived from | TEA |
| Successors | Corrected Block TEA |
| Cipher detail | |
| Key sizes | 128 bits |
| Block sizes | 64 bits |
| Structure | Feistel cipher |
| Rounds | variable; recommended 64 Feistel rounds (32 cycles) |
| Best public cryptanalysis | |
| A related-key rectangle attack on 36 rounds of XTEA (Lu, 2009) | |
In cryptography, XTEA (eXtended TEA) is a block cipher designed to correct weaknesses in TEA. The cipher's designers were David Wheeler and Roger Needham of the Cambridge Computer Laboratory, and the algorithm was presented in an unpublished technical report in 1997 (Needham and Wheeler, 1997). It is not subject to any patents.
Like TEA, XTEA is a 64-bit block Feistel cipher with a 128-bit key and a suggested 64 rounds. Several differences from TEA are apparent, including a somewhat more complex key-schedule and a rearrangement of the shifts, XORs, and additions.
This standard C source code, adapted from the reference code released into the public domain by David Wheeler and Roger Needham, encrypts and decrypts using XTEA:
The changes from the reference source code are minor:
(v0<<4 ^ v0>>5) + v0 ^ sum + k[sum>>11 & 3];
The recommended value for the "num_rounds" parameter is 32, not 64, as each iteration of the loop does two Feistel-cipher rounds. To additionally improve speed, the loop can be unrolled by pre-computing the values of sum+key[].
In 2004, Ko et al. presented a related-key differential attack on 27 out of 64 rounds of XTEA, requiring 220.5chosen plaintexts and a time complexity of 2115.15 (Ko et al., 2004).
...
Wikipedia