Tiny Encryption Algorithm
|
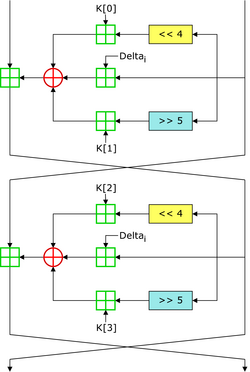
Two Feistel rounds (one cycle) of TEA
|
|
| General | |
|---|---|
| Designers | Roger Needham, David Wheeler |
| First published | 1994 |
| Successors | XTEA |
| Cipher detail | |
| Key sizes | 128 bits |
| Block sizes | 64 bits |
| Structure | Feistel network |
| Rounds | variable; recommended 64 Feistel rounds (32 cycles) |
| Best public cryptanalysis | |
| TEA suffers from equivalent keys (Kelsey et al., 1996) and can be broken using a related-key attack requiring 223chosen plaintexts and a time complexity of 232. The best structural cryptanalysis of TEA in the standard single secret key setting is the zero-correlation cryptanalysis breaking 21 rounds in 2121.5 time with less than the full code book | |
In cryptography, the Tiny Encryption Algorithm (TEA) is a block cipher notable for its simplicity of description and implementation, typically a few lines of code. It was designed by David Wheeler and Roger Needham of the Cambridge Computer Laboratory; it was first presented at the Fast Software Encryption workshop in Leuven in 1994, and first published in the proceedings of that workshop.
The cipher is not subject to any patents.
TEA operates on two 32-bit unsigned integers (could be derived from a 64-bit data block) and uses a 128-bit key. It has a Feistel structure with a suggested 64 rounds, typically implemented in pairs termed cycles. It has an extremely simple key schedule, mixing all of the key material in exactly the same way for each cycle. Different multiples of a magic constant are used to prevent simple attacks based on the symmetry of the rounds. The magic constant, 2654435769 or 9E3779B916 is chosen to be ⌊232/ϕ⌋, where ϕ is the golden ratio.
TEA has a few weaknesses. Most notably, it suffers from equivalent keys—each key is equivalent to three others, which means that the effective key size is only 126 bits. As a result, TEA is especially bad as a cryptographic hash function. This weakness led to a method for hacking Microsoft's Xbox game console, where the cipher was used as a hash function. TEA is also susceptible to a related-key attack which requires 223chosen plaintexts under a related-key pair, with 232 time complexity. Because of these weaknesses, the XTEA cipher was designed.
...
Wikipedia