Nmap
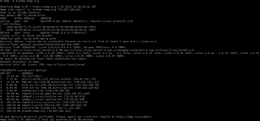
results of an Nmap scan
|
|
| Original author(s) | Gordon Lyon (Fyodor) |
|---|---|
| Initial release | September 1997 |
| Stable release |
7.40 / 20 December 2016
|
| Repository | github |
| Development status | Active |
| Written in | C, C++, Python, Lua |
| Operating system | Cross-platform |
| Available in | English |
| Type | computer security, network management |
| License | GPL v2 |
| Website | nmap |
Nmap (Network Mapper) is a security scanner, originally written by Gordon Lyon (also known by his pseudonym Fyodor Vaskovich), used to discover hosts and services on a computer network, thus building a "map" of the network. To accomplish its goal, Nmap sends specially crafted packets to the target host(s) and then analyzes the responses.
The software provides a number of features for probing computer networks, including host discovery and service and operating-system detection. These features are extensible by scripts that provide more advanced service detection, vulnerability detection, and other features. Nmap can adapt to network conditions including latency and congestion during a scan. The Nmap user community continues to develop and refine the tool.
Nmap started as a Linux-only utility, but porting to Windows, Solaris, HP-UX, BSD variants (including OS X), AmigaOS, and IRIX have followed. Linux is the most popular platform, followed closely by Windows.
Nmap features include:
Nmap can provide further information on targets, including reverse DNS names, device types, and MAC addresses.
Typical uses of Nmap:
NmapFE, originally written by Zach Smith, was Nmap's official GUI for Nmap versions 2.2 to 4.22. For Nmap 4.50 (originally in the 4.22SOC development series) NmapFE was replaced with Zenmap, a new official graphical user interface based on UMIT, developed by Adriano Monteiro Marques.
...
Wikipedia
